Understanding the Palo Alto Networks Platform Strategy
Can any company imitate Palo Alto Networks competitive advantage?
If there is a single metric to measure the effectiveness of a company’s total spend on cybersecurity then that is the rate of prevention, yet breach happens nearly every month. In this article, I want to spend time analyzing the strategy of one of the biggest players in cybersecurity. I will first define what platform means in the context of cybersecurity, and then go on to how Palo Alto Networks (PAN) is executing on this strategy. Finally note that PAN went from a pure-play firewall company some 5-7 years ago to a platform company today; and they did that by acquiring 19 companies in three main product areas - network security, cloud security and security operations. This indicates on the long-term play that PAN has embarked on and is executing well on.
Definition of a Platform
The threat environment is fluid and the threat actors are technically advanced. As a customer, you then want the ability to be present everywhere at all times to detect and prevent an attack. To be inserted into the ‘attack kill chain’ or the lifecycle of an attack means to have the ability to monitor threats in the network, endpoints, cloud or where ever the data resides. The only way to do this is to have a unified security platform, which brings together employees, policies, data and devices. This is the definition of a security platform. Customers will come to expect high degree of prevention, less human involvement and more automated tasks. There are two key reasons why executing a platform strategy is difficult to imitate.
First, complexity increases human involvement. Complexity also breaks automation. Complexity is what kills platform approaches. Therefore the need of a simplified security platform that can deliver on its promise of effectiveness in preventing attacks. The company that will be best positioned to win with this approach will be one that has unified its point solutions to a platform and can deliver on the promise of effective security. This means unified policy - a promise that only few can deliver across a product portfolio. Further, it also needs a single management pane to deploy and operate.
Second, a platform by nature increases stickiness as it entwines a company’s people, policy, data and machines/devices and solves for multiple use cases. In this scenario, integration of the various products in the companies arsenal is paramount to demonstrating value of the platform. Additionally, only a company with a proven track record of technical excellence in multiple product lines can be chosen by large enterprises to offer a platform strategy. This leaves only a very select list of vendors to offer a platform strategy. Palo Alto Networks is well positioned to be one of them. As the previous Palo Alto Networks (PAN) CEO Mark pointed out very clearly in 2017 to the analysts on why PAN is best positioned to be a platform player in the future:
‘..we're proving that the consistency of having the same kind of security not only to network but also in endpoints and cloud is absolutely critical, and will grow in criticality over time. And very few vendors are going to end up being able to make those claims that they can do that, high rates of prevention exactly the same way everywhere where the data may be….. And as routes to market become open to security innovators, that would not be able to go build businesses and reach scale and get the data importantly themselves is they could -- that we have because we have it in massive amounts.
Palo Alto has been very well known for bringing the highest levels of security into the enterprise space for a long time. And as a result of that, I think we're the premium provider in terms of innovation, and we're not the cheap providers in the market from a price perspective. So our customers pay for value, and we believe we're delivering very high value.
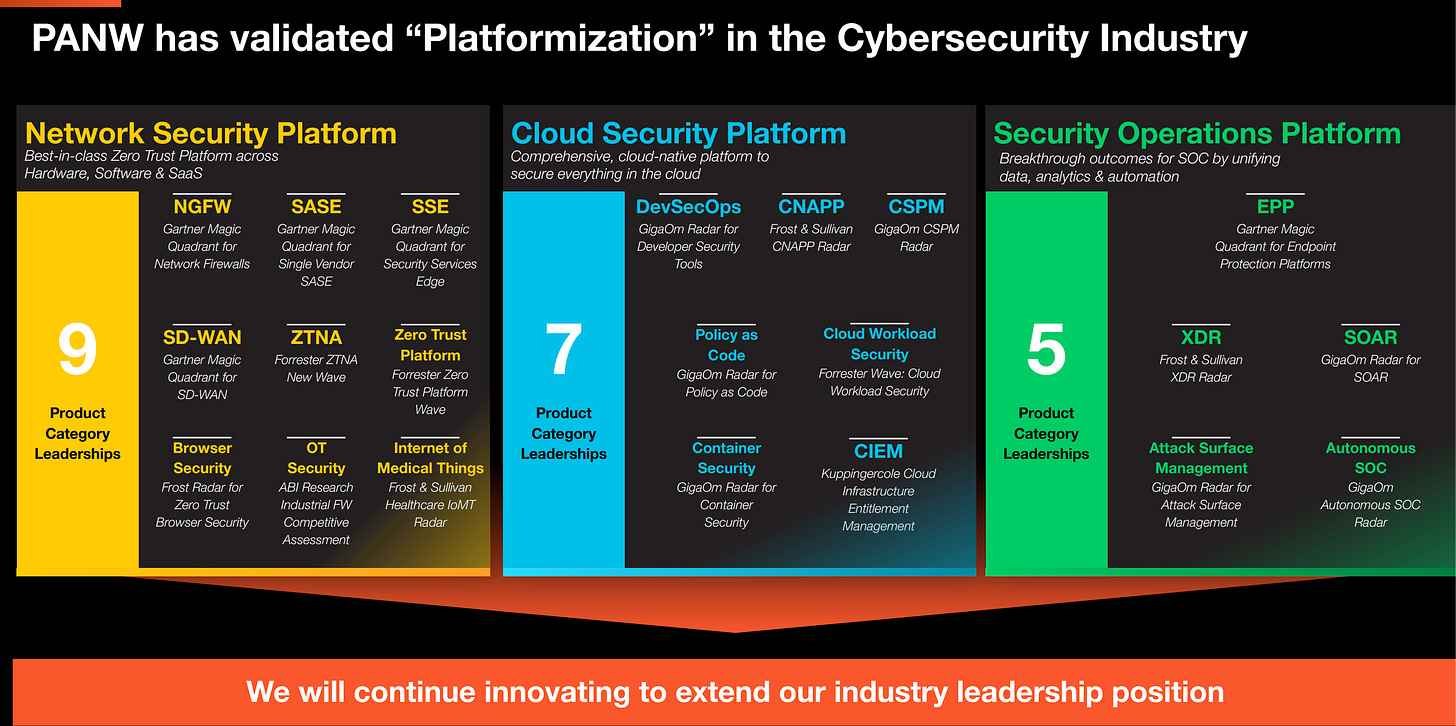
Best of Breed vs Platform Debate
It is common in security industry that most best of breed tools are innovative startups that are born in the current or near-current context of challenges faced in cybersecurity. CISOs with big cybersecurity budget, would typically try to have the best of the breed capabilities based off the Gartner Magic Quadrant. But still they face breach and fail to see successful attack prevention rates.
Thus its safe to assume PAN wants to fulfill the security needs of the deep-pocketed large enterprises. They are a premium player with a track record of leadership in multiple product categories, indicating they are close to capability of a best-of-breed or are the best-of-breed in some of these product categories.
Strategic Execution
So how does PAN plan to execute the platform strategy? After combing through years of PAN’s tech conferences, analyst discussions and quarterly results, this is what I could glean about the execution of the PANs Platformization strategy.
Lead with SASE: To begin with, PAN leads with SASE for customers trying a private access replacement. Why would a firewall company lead with SASE? Well, a typical hardware firewall license is for about 6-7 years. Whereas a SASE license is 1, 2 or 3 years at best. Its much more easier to convince an enterprise customer closer to the end or mid of their 3 year license, than convincing a customer with a much longer hardware firewall contract. Now that the ideal customer profile is defined, we can look at what stands between switching to PAN platform as opposed to going the best-of-breed way or legacy platform way.
The execution of the platform strategy needs to tackle three main obstacles. First, the product platform needs to demonstrate value, which can be proven in terms of detection and prevention of attacks. Second, the various products in the platform needs to be integrated internally to form a single solution stack. The burden to knit together the people, policy, user and device security should be abstracted away from the customer. This can be done by internally creating a single management plane (~single pane of glass) to deploy, observe, monitor, triage and operate the platform. Customer just needs to access that one portal. For any support issues there is one vendor.
Finally in order to execute the platform strategy, the platform player needs to be able to convince customers to rip-and-replace their legacy solution with PAN platform instead of multiple vendor solutions. As per a recent Morgan Stanley research, a typical large organization needs some 50-100 point security tools. To consolidate that management complexity with a single or few vendors would be any enterprise customers dream. PAN knows this and executes well on integrating all its acquisitions to create that one true platform.
Go-To-Market and Switching Costs
Palo Alto Networks CEO Nikesh Arora mentioned how on a weekly basis he speaks to the sales representatives of its top 300 enterprise customers and assesses their plan to replace the existing solutions with PANs’ platform. Out of the 3000 odd sales people at PAN, many of them listens to these calls and share how they can learn from each other to further the platform strategy. Additionally, to ease customers into trying PAN platform, the company is willing to assume the economic risk of transition and provide the support to migrate from legacy tools to PANs platform. Once the value is proven and customers get the long runway to learn the PAN products, they find it much more easier to sign the contract with PANs platform.
This is a long-term play with focus on customer satisfaction, demonstrated via high-quality products for which customers are willing to pay a premium price.
Conclusion
Platformization strategy can be played only if the internal teams executing it are in tandem and the leadership is willing to wait to reap the dividends when the customers finally transition and start paying for the services consumed. It is not an easy to imitate strategy for any of the existing players who haven’t put in the engineering integration work to unify its point products into one platform.
Finally, PANs platform strategy is for the large enterprises with the willingness to pay premium price to reduce complexity and increase efficacy of their cybersecurity spend. This hints to the presence of a large and an often ignored ‘global, long tail’ of mid-market and SMB businesses that have an unmet need for a low-cost platform vendor, with enough performance to meet their unique needs. The secret is always in execution.



